- CyberBakery
- Posts
- Is the Purdue Model Obsolete in the Era of IoT and Cloud Industrial Control Systems(ICS)?
Is the Purdue Model Obsolete in the Era of IoT and Cloud Industrial Control Systems(ICS)?
The Purdue Model remains relevant in certain contexts, though its applicability and utility have evolved over time. It remains relevant as a foundational framework, especially in legacy environments and for understanding industrial network segmentation. However, in modern, highly interconnected industrial environments, it must be adapted to account for new technologies and operational paradigms.
Theodore J. Williams and the Purdue University Consortium introduced the Purdue model as part of the Purdue Enterprise Reference Architecture (PERA), in 1992. The model is a definitive reference for data flows in computer-integrated manufacturing (CIM), where plant processes are fully automated. It establishes the standard for designing an industrial control system (ICS) network architecture prioritising operational technology (OT) security. By clearly separating the layers of the network, it facilitates a hierarchical flow of data, ensuring robust security measures are in place.
The Purdue Model
This model is a comprehensive framework for understanding the interconnections among the fundamental components of typical Industrial Control System (ICS) architecture. It categorises these components into six distinct zones, which encompass both Information Technology (IT) and Operational Technology (OT) systems. This highlights the need for an integrated approach to security and performance.
OT systems occupy the lower levels of the model, while IT systems occupy the upper levels, with a “demilitarised zone” of convergence between them. Let’s examine each zone in the Purdue reference model, top to bottom.
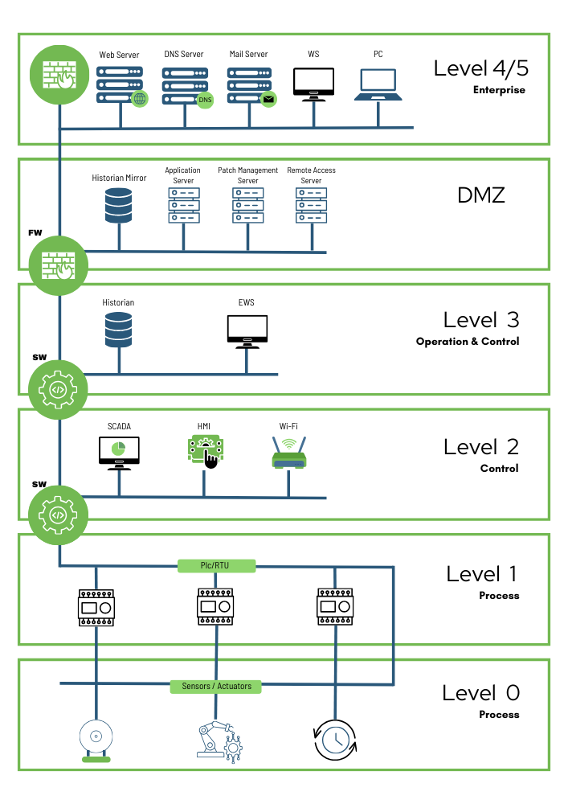
Figure 1 Purdue Model
Level 4/5: Enterprise Zone
These zones encompass the vital IT network that supports the business's primary operations, playing a crucial role in coordinating manufacturing processes. Within this environment, Enterprise Resource Planning (ERP) systems function as the backbone, meticulously managing production schedules, optimising material usage, facilitating shipping logistics, and tracking inventory levels to ensure smooth operations.
Any disruptions occurring in these zones can lead to significant downtime, posing a serious threat to the organisation. Such interruptions could result in considerable economic losses, jeopardise the integrity of critical infrastructure, and ultimately impact revenue generation, highlighting the importance of maintaining continuous and reliable operations.
Level 3.5: Demilitarised Zone (DMZ)
This security zone is composed of essential systems, including firewalls and proxies, specifically designed to thwart lateral movement of threats between IT and OT environments. As automation continues to grow, the demand for seamless, bidirectional data exchanges between IT and OT systems becomes increasingly vital. This convergence layer not only offers organisations a potential competitive edge by streamlining operations and enhancing efficiencies, but it also poses a heightened cyber risk, particularly if organisations implement a flat network architecture that lacks sufficient segmentation and security controls.
Level 3: Manufacturing Operations Systems Zone
This zone is equipped with customised OT devices that effectively manage production workflows on the shop floor.
Manufacturing operations management (MOM) systems manage production operations.
Manufacturing execution systems (MES) collect real-time data to help optimise production.
Data historians store process data and (in modern solutions) perform contextual analysis.
Disruptions at this level are similar to Levels 4 and 5 and will unequivocally lead to economic damage, the failure of critical infrastructure, risks to both people and plant safety, and significant revenue losses.
Level 2: Control Systems Zone
This zone encompasses various systems designed to oversee, monitor, and regulate physical processes. These systems work together to ensure that operations run efficiently and effectively, providing real-time data and control to maintain optimal performance in various environments:
Supervisory control and data acquisition (SCADA) software oversees and controls physical processes, locally or remotely, and aggregates data to send to historians.
Distributed control systems (DCS) perform SCADA functions but are usually deployed locally.
Human-machine interfaces (HMIs) connect to DCS and PLCs to allow for basic controls and monitoring.
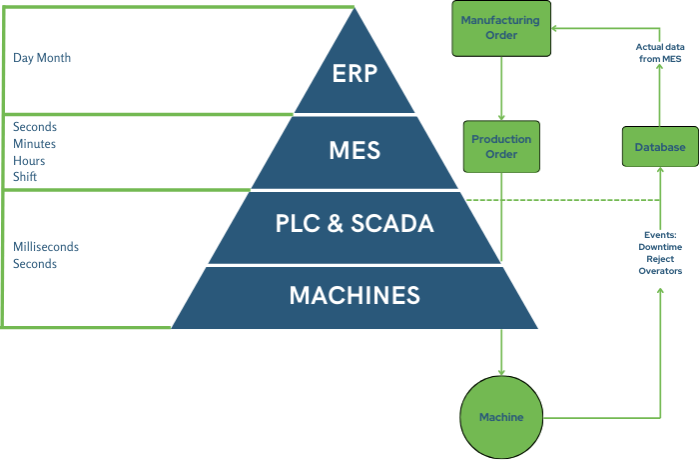
Figure 2 Purdue Model-Data Flow
Level 1: Intelligent Devices Zone
This zone contains instruments that send commands to the devices at Level 0:
Programmable logic controllers (PLCs) monitor automated or human input in industrial processes and make output adjustments accordingly.
Remote terminal units (RTUs) connect hardware in Level 0 to systems in Level 2.
Level 0: Physical Process Zone
This area is equipped with a range of sensors, actuators, and machinery that play crucial roles in various physical processes, including assembly and lubrication. The sensors monitor operations in real-time and relay data to cloud-based monitoring software through cellular networks, enabling seamless communication and oversight. These advanced technologies work together to enhance efficiency and precision within the zone.
When implemented effectively, this model establishes a crucial “air gap” between the ICS/OT environments and the IT infrastructure. This deliberate separation is essential for protecting sensitive operational systems from potential threats that may arise from IT-related vulnerabilities. By creating this gap, organisations can enforce stringent access controls that limit exposure, ensuring that only authorised personnel can interact with the ICS/OT systems.
Furthermore, the air gap allows for the maintenance of operational continuity, meaning that security measures do not impede business processes. This approach not only safeguards critical infrastructure but also supports compliance with industry regulations and enhances overall system resilience. Ultimately, this model promotes a secure, efficient integration of IT and OT, fostering a safer operational environment while maintaining high levels of productivity.
Relevance in Modern Industrial Environments
ICS Design and Segmentation: The Purdue Model is still widely used for designing industrial networks. It helps segment systems into hierarchical layers, ensuring that OT and IT systems remain distinct, which is critical for maintaining security and operational integrity.
Cybersecurity: Cybersecurity frameworks, such as the ISA/IEC 62443 standard, incorporate concepts aligned with the Purdue Model. For instance, defining zones and conduits for network segmentation is rooted in the Purdue architecture.
Legacy Systems: Many existing industrial facilities were built around the Purdue Model, and it continues to influence system upgrades and maintenance.
ICS Cyber Security Challenges
ICS possess unique characteristics that make securing them more complex than traditional IT environments. These systems are deterministic, requiring precise real-time operation. Adding security layers can introduce latency, which is unacceptable in scenarios. For example, in manufacturing environments, an ICS may regulate robotic assembly arms that must operate with millisecond-level precision; even a slight delay caused by security software could disrupt production and result in significant losses. Additionally, many ICS components run continuously, often serving critical functions tied to organisational goals, such as ensuring safety or driving profitability. As a result, any updates or modifications must be carefully scheduled to minimise downtime and service disruption.
Despite handling sophisticated industrial processes, ICS are inherently simple in their function—they perform the specific tasks they were designed for, without additional features. While these systems have significantly improved over time, their evolution has diverged from that of IT systems, leaving their security capabilities comparatively underdeveloped and often overlooked by cybersecurity professionals.
Challenges and Adaptations
The Purdue Model, while historically significant, exhibits notable shortcomings when applied to the rapidly evolving landscapes of digital transformation and Industry 4.0. As organisations increasingly embrace advanced technologies and interconnected systems, the limitations of this model become more evident, necessitating a re-evaluation of its relevance and effectiveness in modern industrial settings:
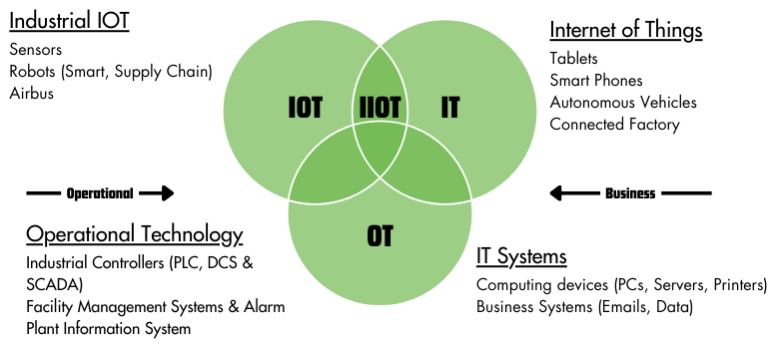
Figure 3 IT-OT Convergence
Industrial Internet of Things (IIoT): IIoT devices fundamentally alter the traditional boundaries between Purdue layers. Data from Level 0 (sensors) is now sent directly to cloud services, effectively bypassing the intermediate levels. This shift represents a significant transformation in how we manage and utilise data in industrial settings.
Cloud Integration: The model's reliance on a hierarchical structure directly undermines its compatibility with cloud-first architectures and edge computing.
Increased Connectivity: Modern OT systems often require real-time communication across traditional Purdue layers, challenging the strict isolation the model suggests.
Zero Trust Architectures: Zero trust principles, which emphasise verifying every transaction regardless of its location within the network, may conflict with the Purdue Model’s implicit trust within layers.
How the Purdue Model is Evolving
Historically, the Purdue Model was significant for its ability to offer clarity and standardisation during a period of rapid technological advancement. It allowed industries to integrate various automation systems while maintaining a consistent operational structure.
However, as technological advancements continue to accelerate, the needs of industry stakeholders are evolving, prompting an evolution of the Purdue Model itself. One of the most significant changes is integrating IIoT and edge computing. These technologies are pushing the boundaries of the Purdue Model by enabling real-time data processing and analysis at the edge of the network rather than relying on central data centres. This shift enhances responsiveness and provides greater flexibility in deploying scalable solutions.
Additionally, cybersecurity concerns have necessitated adjustments within the Purdue Model. The growing prevalence of cyber threats has emphasised the importance of strengthening the model's security protocols, particularly at the intersection of IT and OT. Innovations like zero-trust architectures are being integrated to ensure robust protection against potential vulnerabilities.
Moreover, the rise of artificial intelligence and machine learning is shaping how the Purdue Model is applied. These technologies are being leveraged to automate decision-making processes within industrial environments, allowing for predictive maintenance and optimised resource management. As a result, the Purdue Model is transitioning from a static hierarchy to a more dynamic and interconnected framework that supports self-optimising systems.
The implications of these changes are profound. The evolving Purdue Model offers stakeholders opportunities to enhance operational efficiency and competitiveness. However, it also necessitates investment in new technologies and the development of skills to manage more complex systems. Organisations that successfully adapt to these changes stand to benefit from increased productivity, reduced downtime, and enhanced decision-making capabilities.
The Purdue Model will likely evolve in response to emerging technologies and industry demands. Future developments include deeper integration with artificial intelligence, further enhancements in cybersecurity measures, and the expansion of autonomous systems. The Purdue Model remains a crucial framework as industries navigate these advancements, providing a roadmap for effective technology adoption and business transformation.
Conclusion
In conclusion… Is it obsolete? NO!! The Purdue Model is not obsolete but inadequate on its own to address the needs of IoT and cloud ICS. It remains a useful conceptual framework, especially for:
Legacy Systems: Many facilities still operate on architectures rooted in the Purdue Model.
Initial Planning: It provides a foundational understanding for organising and segmenting industrial networks.
However, in modern environments:
It must be supplemented with more agile, flexible, and dynamic architectures.
Organisations should adopt modern security practices like Zero Trust, distributed processing, and adaptive networking.
The Purdue Model is a valuable starting point but requires significant adaptation to remain relevant in the IoT and cloud-based ICS era.
Reply