- CyberBakery
- Posts
- CyberBakery Chronicles (21 July 2025)
CyberBakery Chronicles (21 July 2025)
Welcome to this week’s edition of CyberBakery Chronicles, your trusted source for the latest news in digital security. Whether you're an enthusiastic novice or a seasoned expert, our insightful content aims to keep you informed and engaged.

Your Weekly Cybersecurity Update (21 July 2025)
Urgent Security Alert: Zero-Day Flaw in CrushFTP Actively Exploited to Take Over Servers
Singapore Bolsters Cyber Defences Against Chinese-Linked Hacker Group UNC3886
Cisco ISE Hit by Critical Root-Level Flaws—Patch Immediately
UAP Data Breach: Massive Cyberattack Exposes Political Party Members’ Private Data
CrushFTP, a popular enterprise file transfer server used by organisations to securely manage and share files using FTP, SFTP, and HTTP/S, is urgently warning customers about a critical zero-day vulnerability. Tracked as CVE-2025-54309, the flaw allows attackers to gain administrative access via the server's web interface on unpatched systems.

Discovery and Exploitation Timeline
The vulnerability was first detected being exploited on July 18, 2025, at 9 a.m. CST, although attacks may have started as early as the previous day. According to CrushFTP, the exploit was possible due to a previously undiscovered bug. Intriguingly, an earlier unrelated security fix involving AS2 in HTTP(S) processes had inadvertently mitigated this new flaw by disabling a rarely used feature by default. However, that fix was not applied with this specific vulnerability in mind.
CrushFTP believes that attackers reverse-engineered the application, discovered the previously unknown bug, and began targeting devices missing recent patches, specifically versions released prior to July 1, 2025. The latest builds—v10.8.5 and v11.3.4_23 or later—are already patched and immune to this exploit. Systems that have kept up with updates are not vulnerable.
Attack Methods and Recommendations
The attack vector leverages the CrushFTP web interface on outdated servers.
It is unclear when the vulnerable versions were publicly available, but they were in use before July 1st.
Enterprise users running a DMZ (demilitarised zone) instance to separate their central server appear to be less exposed. However, security firm Rapid7 urges caution, warning that relying solely on a DMZ is not a durable mitigation strategy.
Indicators of Compromise
CrushFTP advises administrators to look for:
Unexpected changes in the MainUsers/default/user.XML, especially recent modifications to the last_logins field.
The appearance of new, unfamiliar admin-level usernames, like 7a0d26089ac528941bf8cb998d97f408m.
Any unusual changes in the default user configuration, which has been the primary target in observed attacks[1] .
Mitigation Steps
CrushFTP recommends the following actions:
Update immediately to the latest version (v10.8.5 or v11.3.4_23 or above).
Restore user configurations from a backup dated before July 16th if a compromise is suspected.
Review upload and download logs for suspicious activity.
Implement IP whitelisting for server and admin access.
Use or strengthen DMZ instances where appropriate.
Enable automatic updates to reduce future risk.
Broader Implications
At this time, it is unclear whether the exploitation has resulted in data theft or the deployment of malware. The incident reflects a broader trend where managed file transfer solutions, such as MOVEit, GoAnywhere MFT, and Accellion FTA, have become lucrative targets for data theft and extortion campaigns, particularly by ransomware groups.
CrushFTP's response highlights the importance of regular patching routines, as customers who maintained updated systems were protected from this zero-day attack.
Singapore’s national security leadership has publicly disclosed that the city-state is currently under attack by a sophisticated Chinese espionage group targeting its most vital infrastructure networks. The revelation marks a significant escalation in Singapore’s public stance against state-sponsored cyber threats.
Active Threat to National Security
Coordinating Minister for National Security K. Shanmugam revealed during a Friday speech that the hacking group UNC3886 poses a “serious threat” to Singapore and “has the potential to undermine our national security”. The minister emphasised the immediate nature of the threat, stating that “even as we speak, the group is attacking our critical infrastructure right now”.
The attacks are described as both severe and ongoing, with Shanmugam noting that authorities are still assessing whether it would be in Singapore’s interest to disclose additional details about the campaign.

Image: Cyber Security Agency of Singapore
Sophisticated Espionage Operations
Google-owned cybersecurity firm Mandiant has characterised UNC3886 as a “China-nexus espionage group” that demonstrates advanced capabilities in targeting network infrastructure. The group’s operations show several concerning characteristics:
Strategic targeting of high-value assets, including defence, technology, and telecommunications organisations across the United States and Asia
Stealth-focused operations are designed for long-term persistence while minimising detection risks
Custom backdoor deployment on critical network devices, particularly Juniper Networks routers
The hackers have also been observed targeting Fortinet and VMware network devices, indicating broad capabilities across multiple vendor platforms.
Critical Infrastructure at Risk
Singapore’s critical infrastructure encompasses multiple essential sectors, including energy, water, banking, finance, healthcare, transport, government, communications, media, and security and emergency services. Shanmugam warned that successful attacks on these systems could create cascading impacts across Singapore’s economy and society.
“Attacks on our systems and infrastructure will then impact on how we do business, who will be our vendors, and what’s in our supply chains,”
“Attacks on our systems and infrastructure will then impact on how we do business, who will be our vendors, and what’s in our supply chains,” the minister explained, adding that Singapore may be forced to reconsider trusted partnerships if systems cannot be secured.
Pattern of Regional Targeting
This latest disclosure follows previous incidents involving Chinese advanced persistent threat groups targeting Singapore’s infrastructure. The Chinese state hacking group Volt Typhoon is believed to have successfully breached Singapore Telecommunications Ltd., the country’s largest mobile carrier, during the summer of 2024.
The attacks on Singapore are part of a broader pattern of Chinese cyber espionage activities across the Asia-Pacific region. Recent reports indicate that Chinese-linked hackers have also targeted Taiwanese semiconductor companies and investment analysts as part of coordinated cyber espionage campaigns.
Diplomatic Tensions and Denials
China consistently rejects allegations of state-sponsored cyber espionage, maintaining that it opposes all forms of cyberattacks and claims to be a victim of such threats itself. The Chinese embassy in Singapore has not yet provided an official response to the latest accusations.
However, the public nature of Singapore’s disclosure represents a significant diplomatic step, as the city-state typically maintains careful diplomatic balance in its relationships with major powers, including China.
The ongoing campaign highlights the evolving landscape of cyber warfare, where critical infrastructure has become a primary target for state-sponsored actors seeking to gain strategic advantages through digital infiltration and long-term network persistence.
Cisco has sounded the alarm, unveiling a set of critical vulnerabilities in its Identity Services Engine (ISE) and Passive Identity Connector (ISE-PIC)—and the stakes could not be higher. A troubling new bug, tagged as CVE-2025-20337, allows anyone on the internet to seize complete control of affected systems without even logging in.
What’s at Risk?
The flaws are a nightmare scenario for any organisation that relies on Cisco’s platform to manage network access and identity security. Here’s why:
No Login Needed: Attackers don’t require credentials. With a specially crafted API request, they can remotely execute code as root on vulnerable systems.
Maximum Severity: Each major flaw carries a CVSS score of 10.0, the highest possible criticality rating.
Broad Impact: Affected releases include Cisco ISE versions 3.3 and 3.4 and ISE-PIC counterparts. Earlier versions (3.2 or earlier) dodge the bullet.

How Attackers Take Over
Input Validation Fail: The main culprit behind CVE-2025-20337 and its sibling, CVE-2025-20281, is the insufficient validation of user-supplied input in Cisco’s API. Hackers can exploit this by sending malicious requests—no password or prior access required.
File Upload Danger: A related flaw (CVE-2025-20282) allows adversaries to upload arbitrary files and execute them with root privileges, again, with no authentication barrier.
If Unpatched, You Face…
Total Compromise: Full system takeover—attackers can steal data, move laterally across the infrastructure, or wipe out systems altogether.
Supply Chain and Compliance Risks: Since ISE is widely used in critical sectors, a breach could ripple through partners, compliance frameworks, and public trust.
What You Need to Do—Right Now
Cisco’s message is clear: patch and patch quickly. Here’s your instant to-do list:
Upgrade Immediately:
For Cisco ISE 3.4, ensure you are on Patch 2 or later.
For Cisco ISE 3.3, upgrade directly to Patch 7. Hotfixes applied earlier are not sufficient.
No Workarounds: There are currently no effective workarounds. Patching is the only mitigation.
Restrict Admin Access: Block all public access to management interfaces and API endpoints until you are patched and protected.
Vigilance After Updating: Monitor your systems for unusual authentication attempts or API activity, and validate system integrity after the upgrade.
Why This Matters
Critical vulnerabilities in cornerstone infrastructure, such as Cisco’s ISE, raise the bar for threat response. Whether you’re a small team or a global enterprise, these flaws could open doors for ransomware attackers, espionage groups, or opportunistic hackers. Rapid action isn’t just recommended—it’s imperative.
Take this as a wake-up call: in the world of cybersecurity, even trusted platforms can become attack vectors overnight. Don’t wait—patch, protect, and stay vigilant.
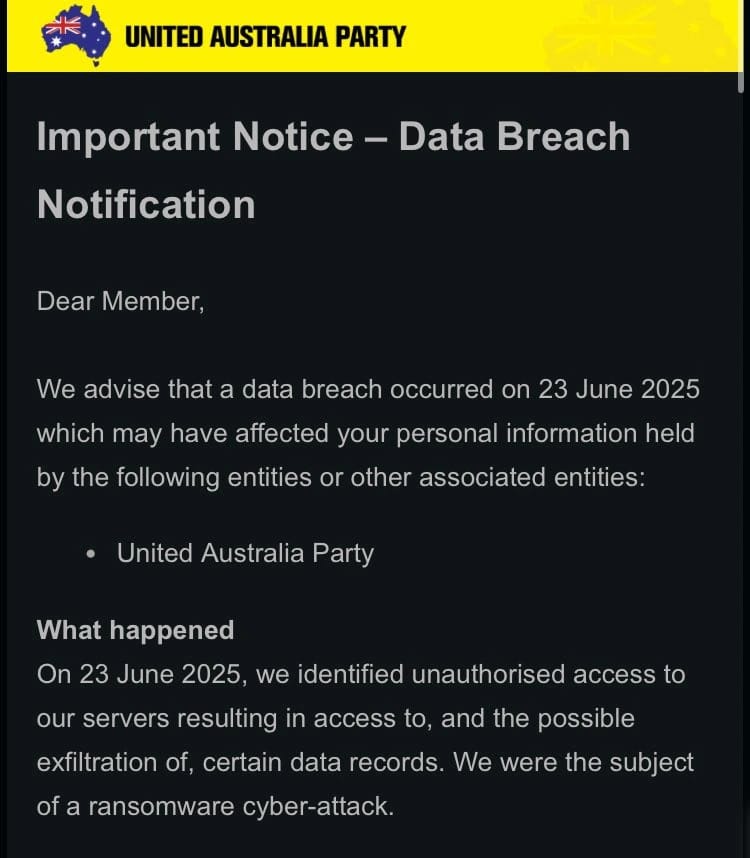
The United Australia Party (UAP), led by Clive Palmer, has confirmed it suffered a major ransomware cyberattack, exposing sensitive personal and financial records of its members, supporters, and contacts. The incident, revealed this week, also involves the affiliated group Trumpets of Patriots—together named “the Political Parties” in official statements.
What Happened?
On June 23, 2025, UAP discovered that hackers had infiltrated its servers, giving them access to an extensive digital archive:
All emails and attachments sent to or from the Political Parties
Confidential documents and records, dating back as far as the servers that maintained such files
This breach could impact anyone who engaged with UAP or Trumpets of Patriots, including the submission of sensitive documents, personal information, and even bank details.
What Kind of Data Was Exposed?
The cyberattackers may have accessed:
Names, addresses, email addresses, and phone numbers
Banking and identity documents
Employment histories
Any confidential records, including attachments and correspondence
Files provided under confidentiality agreements
UAP admits it cannot determine precisely who is affected or exactly which files were stolen. Tenure or recent involvement with the party doesn’t matter; if you’ve ever corresponded or shared information with them, you could be at risk.
Crucially, UAP revealed, “We do not keep a record of all individuals who were on the server,” making it “impracticable to notify individuals” directly about their exposure.
What Is the Party Doing About It?
UAP reported the attack to the Office of the Australian Information Commissioner and the Australian Signals Directorate as required by law.
Officials have secured affected systems and restored recoverable data from backup tapes.
The party issued a public alert and apology but left individuals to determine for themselves whether their details were at risk.
What Should You Do If You’ve Had Any Involvement?
UAP urges anyone who has interacted with the party to assume their data may have been compromised and to take the following steps:
Scrutinise past communications (email, mail, attachments)
Monitor bank accounts and identity documents for unusual activity
Change passwords and enable multi-factor authentication on essential accounts
Watch for phishing attempts—if you get an email, text or call appearing to be from UAP or Trumpets of Patriots, verify before reacting
Public Reaction and Ongoing Risks
While UAP has apologised, critics have called out the party’s lack of direct notification, stating that telling potentially tens of thousands of people to “figure it out themselves” falls short of reasonable responsibility. Data security experts warn that exposed records can be misused for identity theft, fraud, or targeted scams.
This breach is a stark reminder that political groups aren’t immune to significant cyber threats—and that comprehensive data management and transparency are essential for public trust. Stay vigilant, protect your information, and be alert for suspicious communications if you’ve ever been involved with UAP or its affiliates.
Cybercriminals are escalating their exploitation of trusted developer platforms, with GitHub now under siege as a channel for distributing sophisticated malware through botnet-driven campaigns. Recent research highlights how threat actors are weaponising public repositories to deliver payloads for notorious infostealers and remote-access trojans, bypassing many traditional security protections.

How the Attack Works
Fake GitHub Accounts: Hackers create bogus GitHub profiles, often with legitimate-sounding usernames, to host malicious files and scripts. These accounts may each contain hundreds of repositories, but each repo typically carries just a single, weaponised payload.
Multi-Stage Infection Chains:
Initial infections often come from loaders like Emmenhtal (also known as Peaklight), which are distributed via phishing or malvertising.
The loader fetches secondary malware directly from fake GitHub repositories, dropping tools such as Amadey, Lumma Stealer, RedLine Stealer, Rhadamanthys Stealer, or remote access trojans, including AsyncRAT.
Legitimate Disguise: Malware files are disguised as benign software or updates, leveraging GitHub’s reputation as a trusted resource. This enables them to slip past many corporate web filters and endpoint protections.
Bypassing Security Controls: Since enterprise systems often whitelist GitHub, the attackers easily circumvent network restrictions, making it tough for security teams to detect malicious downloads.
The Malware at the Heart of the Operation
Amadey Botnet: Known for delivering broad-spectrum payloads, this modular bot can download plugins, steal credentials, exfiltrate sensitive files, and drop further malware.
Infostealers and RATs: The campaign heavily leverages established stealers—such as Lumma and RedLine—to capture credentials, browser data, and system information, before sending it to attacker-controlled infrastructure.
Obfuscation and Living-off-the-Land: Attack scripts are often deeply obfuscated, encoding key parts in Base64, and leverage legitimate Windows processes for execution, increasing stealth.
Real-World Impact
These campaigns have compromised large numbers of devices globally—impacting everyone from software developers to unsuspecting users of pirated media sites. Some infections originate through illegal streaming platforms and malvertising schemes, redirecting users through chains of ad servers before landing them on weaponised GitHub repos.
Mitigation: What You Can Do
Scrutinise Repositories: Always check the legitimacy of GitHub repositories and contributors before downloading code or tools.
Restrict Direct Access: Implement restrictive network policies that only allow access to trusted and vetted repositories.
Behavioural Monitoring: Utilise behavioural analytics and endpoint monitoring systems to identify unusual downloads and process launches, particularly those that occur after visiting GitHub links or opening new projects.
Educate Users: Raise awareness about the risks of downloading code from unknown sources—even on reputable platforms like GitHub.
Stay Vigilant: GitHub works actively to take down malicious accounts, but attackers constantly adapt. Ongoing vigilance is required from both individuals and security teams.
In conclusion
The exploitation of GitHub for malware distribution underscores a decisive shift in cybercrime: trusted open-source platforms are now continuous battlegrounds, where attackers blend in with legitimate activity. For organisations and developers, “trust but verify” is not just good advice—it’s essential cyber hygiene.
Quick favour: Let’s spread the value! If you find this newsletter useful, don’t keep it to yourself. 👉 Share it with friends and colleagues who could benefit from it. Remember, one share could spark insight, ignite inspiration, or lead to a breakthrough for someone else.
Let’s make 2025 the year of shared knowledge and community growth.
Reply